Bring Your Own Account (BYOA) — A Managed ClickHouse Service
BYOA from DoubleCloud — What is it, how it works and why you should care
DoubleCloud are proud to announce that we’ve just launched a brand new feature to our platform called BYOA (Bring Your Own Account).
We’d been getting requests from some of our users that, due to compliance issues with GDPR or other privacy laws/requirements around the globe, they’d rather retain full control of their data.
DoubleCloud’s platform is, of course, fully GDPR compliant without requiring our BYOA service, we’ve just added this as an option for those that require total control over their infrastructure due to organizational restrictions (or other reasons).
To facilitate that, users will now be able to connect their own AWS VPC to deploy ClickHouse® and Apache Kafka® directly into their own AWS accounts meaning all computations, data, backups and encryption keys will stay under the customers direct control. We will manage these clusters in the same way even if they are deployed in an external customer’s VPC. That means we will still provide provisioning and adjustment to configuration without downtime, updates of clickhouse and OS, backups, load balancing, monitoring and security.
How DoubleCloud’s BYOA works
When creating a BYOA solution on the DoubleCloud platform, external networks will be used to transmit your data between different cloud resources (such as clusters).
They’ll then connect to the internet via peering connections in much the same way as internal networks do.
The biggest difference however is that the network will be created under your own AWS account and will belong solely to yourself, with all the additional security perks that will obviously bring.
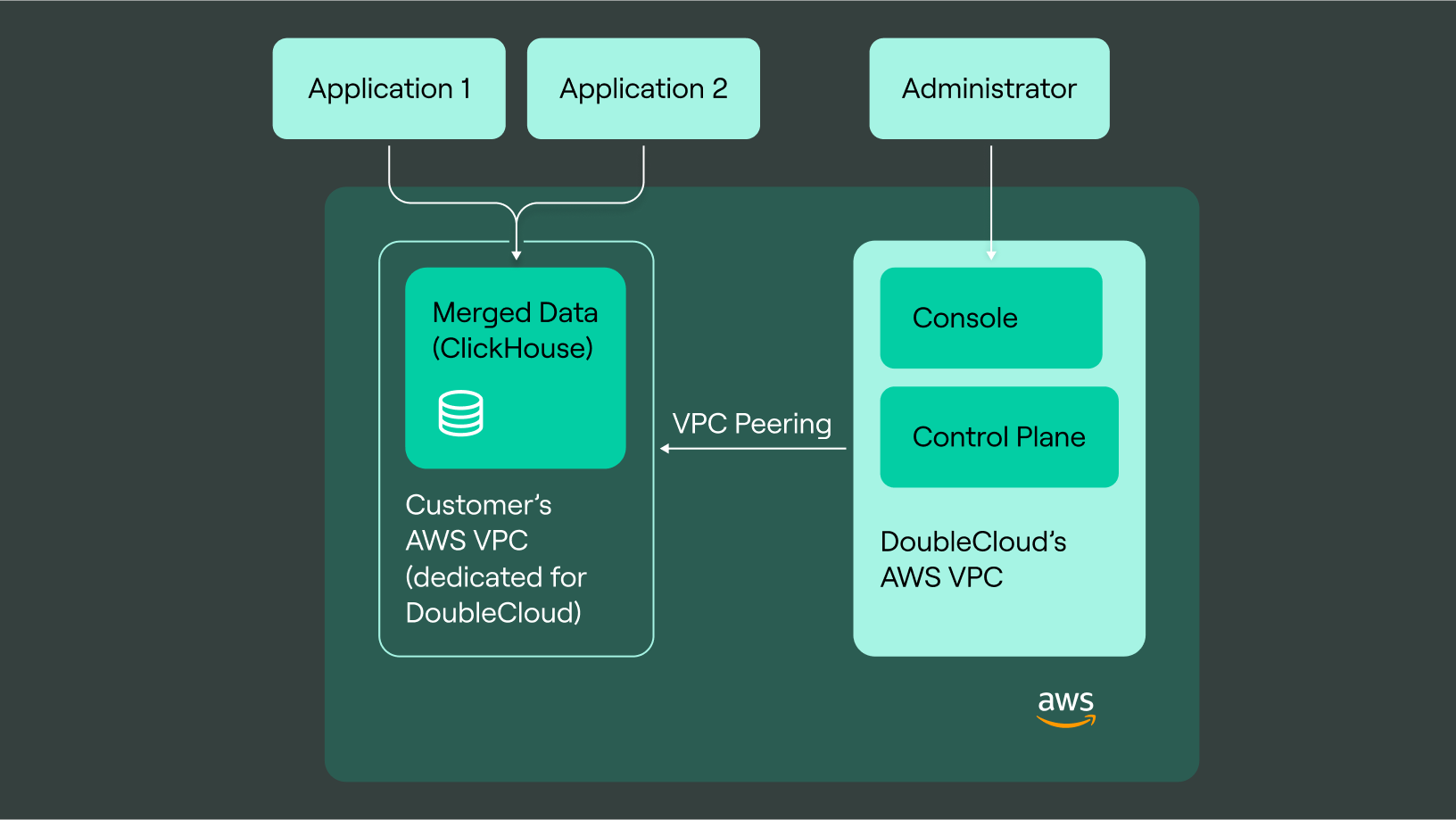
Each network you create will have its own CIDR blocks for both IPv4 and IPv6.
When setting up a ClickHouse or Kafka cluster, it will be created directly within your VPC. You will have full control over the instances there. Also all S3 Buckets needed for backups or hybrid storage will also be created in your AWS environment.
All infrastructure tasks will be done completely within your AWS account. That means resizing, backup or other commands will be started from DCs controlplane via VPC peering directly within your environment.
Why is DoubleCloud’s BYOA important?
First of all, it may not be useful or even desirable to everyone.
This is a specific feature that was requested from a few clients who wanted a greater degree of control over their data due to GDPR and other compliance issues they were facing, as well as certain security certifications that needed to be met.
Others just wanted the ability to be able to configure all their network elements themselves.
Normally when using an external network, you’d manage the computational resources, storage, and data over on the AWS side.
DoubleCloud would then shoulder all the manual, day to day tasks such as backups, monitoring, logs, and anything else that would make the resource management side of things more convenient for our clients.
However, if you use our BYOA option we’ve made available, you’ll handle all network management within AWS, including VPC, subnets, security groups, ALBs, and other elements, as well as any AWS related costs.
Speaking of costs, one of the big benefits of our BYOA model is that if you’ve any special pricing plans, contracts or deals from AWS then they can all still be applied, thus potentially saving you money.
BYOA security
Clusters in external networks will have two levels of protection…
- AWS VPC Security Measures: When you add an external network, DoubleCloud automatically creates several entities under your AWS account. The entities list includes VPC, security groups, ACLs, route tables, and others, depending on your network configuration. These predefined parameters prevent unauthorized access to your network.
- Allow Lists In DoubleCloud: The main manually configurable access management measure is using allow lists for each separate cluster. The allow list prohibits access to the cluster from each IP address except the ones explicitly specified as allow lists entries.
To activate that feature, just follow the instructions here >>
- ClickHouse® is a trademark of ClickHouse, Inc. https://clickhouse.com
- Apache® and Apache Kafka® are either registered trademarks or trademarks of the Apache Software Foundation in the United States and/or other countries.
In this article, we’ll talk about:
Start your trial today