Security practices at DoubleCloud
Every team in the DoubleCloud ecosystem has the resources and opportunity to achieve great things. Our mission is to be instrumental in discovering and empowering the potential in every team of all sizes and industries and, in turn, help advance human progress with cloud solutions.
This realization puts customer trust at the center of what we do. It is the reason why we put security as our paramount priority. We are fully transparent with our security program to ensure you feel informed and secure using DoubleCloud.
Read more about our security approach and learn how customers can participate in our security practices.
Our Approach to Security
In this section, we discuss DoubleCloud's approach to security. It covers the key steps and controls we implement across multiple security domains. These measures cover securing our cloud infrastructure, services, and the relevant security processes we have in place to ensure we effectively secure products for our customers and users.
Our Security philosophy
We employ two basic approaches to security:
-
Meet our customer requirements for cloud security, security standards, and certification requirements.
-
Openness and transparency about our programs, processes, and metrics.
This section highlights the range of measures and initiatives we have in place to fulfill this philosophy as covered by these critical themes.
Our team
Our mission is to enable the business to succeed while being as secure as possible. We achieve this through risk management, employee empowerment, and a security-conscious culture.
The security team provides essential security compliance and operational services. It's directly engaged in the development and release processes. It offers consultative and advisory services to enable the business to function and scale better while minimizing risks.
To reflect this, we built the Information Security team around three fundamental tenets driving our team's structure and activities:
-
Secure DoubleCloud's Product & Platform.
The Security Engineering Team is responsible for the security of our products, billing services, add-ons, and platforms.
-
Protect DoubleCloud and its Employees.
The Security Operations Team is responsible for detecting and responding to security incidents, adversary emulation, Security Intelligence, and internal security concerning our corporate network and applications.
-
Assure DoubleCloud Customers.
The Security Assurance Team tracks and responds to customer expectations and provides transparency into our processes and practices. We foster the understanding of security best practices among our employees and customers.
Our security team's continuing mission at DoubleCloud is to achieve better security. We aim to be among the leaders in cloud security, provide and ensure all the cloud security requirements of our customers, and meet and exceed the security standards and certifications in the industry. We constantly make it clear to all our staff throughout their time with us. We publish all the materials on protecting the data with which our customers entrusted us. We share this mission statement with all our staff throughout their time at DoubleCloud.
Additional programs we use to support security
Building on the security fundamentals, we implement a range of practices to ensure our security approach remains widespread and proactive:
-
Security champions program
We have security contacts within our product engineering teams who assume responsibility for delivering key security initiatives among their peers continuously and communicating with our central security team as openly as possible. This way, we maintain security front and center of mind across our organization.
-
Vulnerability disclosure program
Our Vulnerability Disclosure Policy enables us to leverage a trusted community of researchers to test our products constantly and report any vulnerabilities they find.
Continuous improvement
We aim to ensure our security program remains best in class in the industry. To achieve this, we continuously evaluate our security program and identify opportunities for improvement. Findings from these activities are used to address any gaps and are also opportunities for improvement.
We established and used SLOs and SLIs to identify areas for improvement across each of our core systems.
Securing our internal environment
A practical approach to security starts with getting our own house in order – specifically by keeping our internal environments secure. We take the following steps to achieve this:
Building security into our network architecture
DoubleCloud uses a multi-tiered approach to securing our networks. We implement controls in our cloud environments, separating our infrastructure by environments and services.
We also limit connectivity between our production and non-production environments. We do not replicate production data outside of production environments. Access to production networks and services is only possible within that same environment.
We utilize a network allowlist to authorize services to communicate with other services explicitly. We control access to sensitive networks through virtual private clouds (VPC) routing, security group rules, and access control lists, with all connections into those networks encrypted. We've also implemented intrusion detection in all our networks to detect potential compromises.
Securing access to our networks
DoubleCloud secures access to its corporate network, internal applications, and cloud environments through a Zero Trust concept. DoubleCloud approach to Zero Trust ensures that users can access resources and services on our networks. It is a decision based on their authentication credentials and a dynamic policy decision. This policy considers a range of factors to allow or deny access depending on the security posture of an employee's device (regardless of their location).
DoubleCloud's Zero Trust implementation uses a range of automated processes, services, and components. At a high level:
-
Our identity management service grants authenticated users on corporate devices a certificate, which is deployed onto devices using our endpoint management solutions, and are reissued or revoked regularly.
-
When a user authenticates into our infrastructure, a certificate is issued and used to verify that the user's account is valid and what device they have. Devices connected to DoubleCloud's network are polled periodically and automatically assessed to determine their ownership, device security, and posture information. Security posture requirements include ensuring devices meet minimum requirements, including anti-malware, encryption, and OS versions.
-
Mobile Device Management tools automatically synchronize with a central database with the compliance posture of user devices.
Secure access management
DoubleCloud has established a well-defined user access provisioning workflow for all its services and subcomponents linking our HR and access management systems. We use a role-based access restriction system based on user profiles. This system ensures that staff only have access to resources and data necessary to fulfill the scope of their role in the team.
Supporting our Zero Trust architecture, we control access to our corporate applications through a single-sign-on (SSO) platform. To access any of our applications, staff must authenticate via this platform, including through a second authentication factor. Employees must authenticate using phish and man-in-the-middle attack-resistant second factors.
Securing our endpoint devices
DoubleCloud uses its endpoint management solutions to deploy updates and patches to endpoint operating systems and critical applications. We have also implemented an endpoint protection solution to protect against malware threats.
DoubleCloud staff who wish to access most of our services via personal mobile devices must enroll in our Mobile Device Management (MDM) Program. This security policy enables us to ensure that all devices connecting to our network meet our minimum security requirements, such as encryption, device locking, anti-malware software, OS versions, and necessary security updates.
Security in our day-to-day operations
We strive to build security into all aspects of our day-to-day operational processes.
Managing changes in our environment
Our change management process requires one or more peers to review each code or infrastructure change to identify any issues the change may inflict. We have a procedure to increase the number of reviewers depending on how critical the change or the impacted systems are. We trust our engineers to identify and flag issues before applying the change to the production environment.
This process reliably provides a dynamic and adaptable way of managing environmental changes.
Suppose the change introduces components that do not successfully pass integration, function, unit, or security tests. In that case, the build is rejected and returned to the issuer to address the discovered issues.
Managing configurations in our systems
We have a limited group of engineers who have permission to install the software in our production environment. We employ configuration management tools in our environments to manage server configurations and changes to ensure the immutability of our infrastructure.
For consistency, we overwrite all direct changes made to systems in the production environment by the approved configuration. We push this configuration through the configuration management tools. We rely on standard images, and all changes to Images or operating systems must comply with our standard change management procedures. All exception configurations are subject to tracking and reporting.
We configure our change management process to allow multiple reviewers to approve all configuration changes through configuration management tools before deployment. We require all builds to be cryptographically signed before they are allowed to run in our production environment.
Log management
Logs are a crucial component of our overall incident detection and response strategy. DoubleCloud uses the SIEM platform to aggregate logs from various sources. This platform also applies monitoring rules to aggregated logs and flags suspicious activity.
Each DoubleCloud sub-system has read-only logs, which they forward to the central logging repository. Based on the aggregated logs data, DoubleCloud Security Team creates alerts and monitors for indicators of compromise in our security analytics platform. Our internal processes define the triaging of these alerts, investigating them, and appropriately escalating them if necessary.
We retain logs for 30 days in an instantly retrievable tier and 365 days in an archival tier.
Business continuity and incident recovery management
The resiliency of our products is a crucial concern here at DoubleCloud. We are determined to integrate processes to handle disruptions with minimal customer impact. Our business resilience (BR) and incident recovery (IR) programs capture the various activities to meet those objectives.
We aim to strike a harmonious balance between cost, benefits, and risk by evaluating our services from the recovery time objectives (RTO) and recovery point objectives (RPO) standpoints. The active participation of DoubleCloud leaders in business continuity and disaster recovery planning activities guarantees the necessary supervision to ensure that all teams share resiliency responsibility.
Our BR and IR programs involve the following activities:
-
Building-in redundancy measures to meet resiliency requirements
-
Testing and verifying those redundancy measures
-
Learning from tests to continuously keep improving BC and DR measures.
We design our products to fully leverage redundancy capabilities, such as our cloud service providers' availability zones and regions.
Site Reliability Engineers play a vital role in recognizing gaps in our IR program and collaborating with the risk and compliance team to address them. We regularly monitor numerous metrics to identify potential problems at an early stage. Alerts are set up based on these metrics to notify SREs or the appropriate product engineering teams when thresholds are exceeded, allowing our security team to respond quickly through our incident response procedure. Each team also has a designated DR champion to supervise and assist with disaster recovery related to their respective team.
Our IR tests examine process and technology aspects, including relevant process documentation. The frequency of IR tests aligns with the criticality level of each service. For instance, we perform backup and recovery tests for critical customer-facing systems quarterly.
Our tests include manual and ad-hoc failover tests, ranging from simple tabletop simulations to more complicated availability zone or regional failover tests. Regardless of the test's complexity, we meticulously document test results, analyze potential improvements or gaps, and address them through our internal ticketing system to ensure we improve the process.
We conduct periodic Business Impact Assessments (BIAs) to assess the risks impacting critical services. The output of these BIAs assists in driving the strategy for IR and BR efforts.
Service availability
In addition to the above measures, we publish our service availability status
Backups
We operate a comprehensive backup program at DoubleCloud, that includes our internal systems, whose backup measures are designed to comply with robust system recovery requirements. We also have extensive backup measures for our DoubleCloud Cloud offerings, explicitly referring to customer and application data.
We replicate backup data to multiple data centers within a particular AWS region, and it is not stored offsite. We frequently test our backups to ensure they meet our recovery requirements.
Physical security
Our office's physical security measures follow our physical and environmental security policy, which ensures comprehensive physical security implementation in both on-premise and cloud environments. This policy encompasses securing work areas, safeguarding IT equipment, limiting building and office access to authorized personnel, and monitoring entry and exit points.
Our physical security protocols include manned receptions during business hours, visitor registration requirements, badge access to restricted areas, and collaboration with office building management for after-hours access and video recording at all entry and exit points, including main entrances and loading areas.
Our Cloud Service Providers meet the SOC 2 compliance standard at a minimum, which covers a range of security controls, such as physical and environmental security and protection. Access to the data centers is restricted to authorized personnel and verified through biometric identity verification. Physical security measures include:
-
On-premises security guards.
-
Closed-circuit video monitoring.
-
Man traps.
-
Additional intrusion protection measures.
Keeping data secure
We employ multiple measures to keep customer data secure and available. We also have controls that enable customers to retain control over their data to the fullest extent possible.
Data centers
DoubleCloud uses the services of the industry-leading cloud provider, Amazon Web Services (AWS), to host our products and data, thus achieving optimal performance with redundancy and failover options globally.
We utilize multiple geographically diverse AWS regions (US-East, US-West, European Union, and Asia Pacific) and multiple availability zones within each region to guarantee that a data center failure does not compromise the availability of our products or customer data. For further information, refer to our paper on how DoubleCloud manages customer data.
Encryption of data
DoubleCloud cloud products protect customer data from unauthorized disclosure or modification by encrypting it in transit using TLS 1.2+ and Perfect Forward Secrecy (PFS). We encrypt data at rest using the AES 256 encryption standard. We use strong ciphers and key lengths where supported by the browser.
Key management
DoubleCloud uses the AWS Key Management Service (KMS)
Tenant separation
DoubleCloud's managed services offer customers a shared cloud-based IT infrastructure. However, we have implemented measures to ensure logical separation so that one customer's actions cannot compromise the data or services of other customers.
Sharing the responsibility for managing customer data
DoubleCloud assumes responsibility for our applications' security, availability, and performance, the infrastructure they run on, and the environments they host.
However, security is a joint responsibility between DoubleCloud and our customers concerning four areas in particular:
-
Policy and compliance
Ensuring the system meets customer business needs and operates according to industry, regulatory, and legislative compliance obligations.
-
Users:
-
Creating and managing user accounts.
-
Information.
-
The content customers store within Managed Service for ClickHouse®, Managed Service for Apache Kafka®, DoubleCloud Visualization, and DoubleCloud Transfer.
-
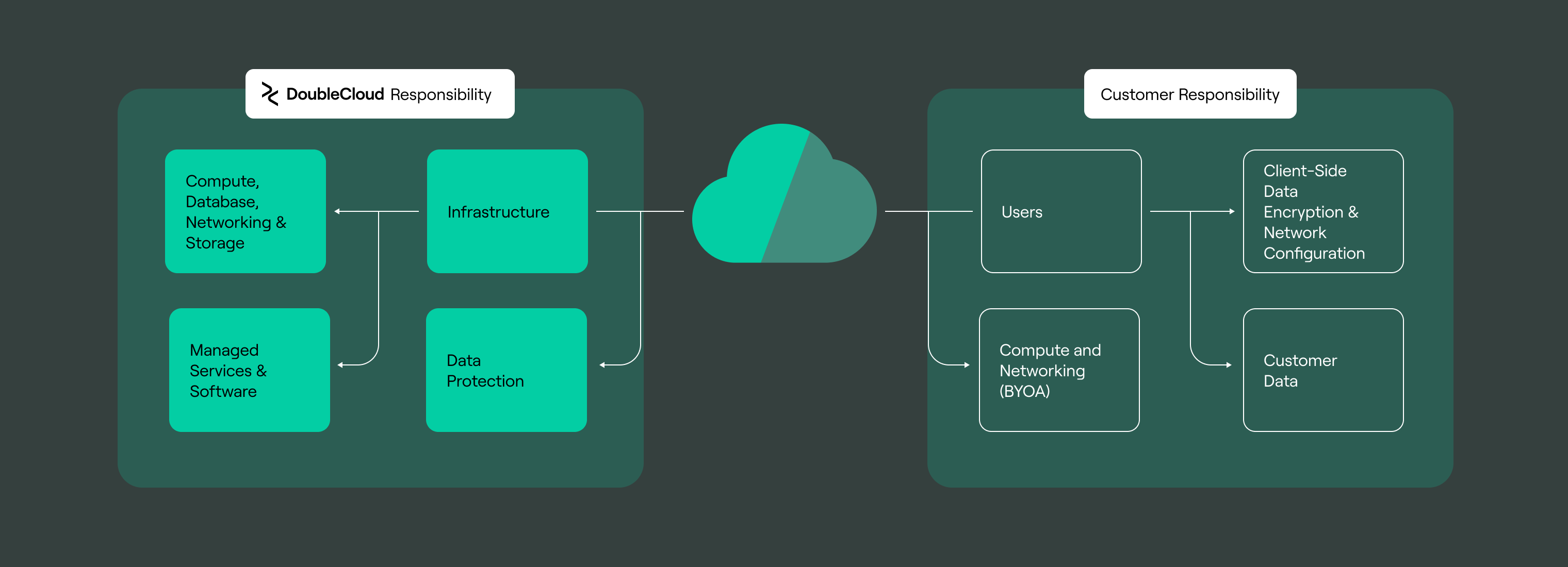
DoubleCloud takes every precaution to secure customer data. However, our customers should understand that their actions also play a crucial role in security implementation. They need to be aware of important factors such as:
-
Access permissions: Our products prioritize collaboration, but customers should be mindful of the access permissions they grant to users within their organization.
-
Centralized access: For enhanced security and centralized administration, using SAML or OAuth for the DoubleCloud console is strongly encouraged, along with enforcing 2FA and single sign-on.
Controlling access to customer data
We take the security of all customer data seriously and have established strict controls for its handling. Our employees and contractors receive training on best practices for handling customer data during onboarding.
Only authorized personnel at DoubleCloud can access customer data stored in our systems. They use individual, ephemeral certificates linked to their identity. Servers only accept SSH connections from DoubleCloud and internal data center locations. Access is limited to privileged groups and is fully audited and recorded.
Our support team provides maintenance and support services. It may access customer data for health monitoring, maintenance, or upon customer request. Customers can grant explicit consent to the support engineer who accesses their data.
Any unauthorized or inappropriate access to customer data is considered a security incident and handled through our incident management process, which includes notifications to affected customers in the case of a policy breach.
Retention and deletion of data
We have provisions to respond to user requests to delete personal information. We also help end users with DoubleCloud accounts delete their personal information.
Customer resources are deactivated within 60 days after a customer's current subscription period ends. DoubleCloud retains data for deleting resources for 7 days (for trial accounts) or 60 days (for paid accounts) after the customer's current subscription ends. Additional information is available on our Security page.
Securing our employees
Fostering a security culture is at the forefront of DoubleCloud's culture. It contributes towards lifting our overall resiliency against potential cyber-attacks. We ensure that our employees can work securely from any location and are empowered to act according to our internal security policies.
Security awareness training
At DoubleCloud, our staff, contractors, and partners undergo comprehensive security awareness training that covers the latest threats, safe work practices, potential security risks, and compliance regulations. This training is mandatory during onboarding and is reinforced continuously to ensure security remains top-of-mind.
In addition to general security training, our developers receive targeted training in secure coding practices.
Our development teams can also access security champions and security engineers for support and guidance on security-related operational tasks.
To encourage open communication and make our security team as accessible as possible, we have established instant messaging channels for easy communication between employees and the security team.
Security champions program
Our product and service teams each have a dedicated security champion committed to promoting security best practices among their team and working with our central security team to enhance communication and collaboration on security matters to facilitate communication flows.
Background checks
We aim only to hire people who will go on to shape the security-embedded culture we have built. As local laws permit, we perform background checks on all new hires.
Securing our products
DoubleCloud is focused on ensuring that security forms a crucial part of all phases of our product life cycles. There are multiple methods we utilize to achieve this.
Security partners
Our security engineering team guides engineering teams and ensures our security software development controls are integrated into the development lifecycle. All our products are supported through this program, with a dedicated Security Partner.
Targeted security assurance
The security engineering team regularly performs security reviews to provide security assurance across our products. A risk-based process prioritizes where to focus assurance activities and identifies what actions are required to mitigate project risk. The following security review activities are performed depending on the identified level of risk, usually in combination:
-
Threat modeling
-
Design review
-
Code review (manual and automated)
-
Security testing
-
Independent assurance using expert third-party researchers and consultants
Secure design through threat modeling
Threat modeling is employed during the design phase to identify security and privacy risks when such projects face complex threats or involve the development of security-critical features. This involves a tabletop/brainstorming session between our engineers, security engineers, and product managers to identify and prioritize relevant threats.
This information is fed into the product design process and ensures appropriate privacy and security controls are implemented. It also enables the security team to perform targeted review and testing in later stages of development.
Code analysis
We use several automated code analysis tools that cover all code repositories at DoubleCloud. These tools run various static and dynamic tests that help ensure our code's overall security. When a pull request is created in a repository, the tools:
-
Find and identify outdated code dependencies that may introduce vulnerabilities.
-
Identify any accidental or inadvertent disclosure of secrets in code repositories.
-
Undertake an analysis to identify any code bugs or smells in the application.
Application security checklists
To ensure our products are securely developed, our developers get access to the support they need to continually build their knowledge regarding relevant security issues and threats they must be aware of.
To this end, we maintain internal application security checklists and guides that our developers can refer to whenever required.
Threat identification and response
Security testing
Our security testing approach is based on continuous assurance and regular internal and external penetration tests. This approach enhances our chances of identifying vulnerabilities early. Our testing measures include the following:
-
Internal Security Tests
Our security engineering team performs regular security testing throughout development. Testing consists of code reviews and application security testing, targeting areas of weakness highlighted during risk assessments.
-
External Penetration Tests
We use specialist security consulting firms to conduct white and grey-box, code-assisted, and threat-based penetration tests on our products and infrastructure.
-
Vulnerability Disclosure
We also use the community of trusted security researchers to continually identify vulnerabilities in our products.
Any security vulnerabilities identified are tracked in our internal ticketing tool. Findings are triaged and tracked according to our Vulnerability Management Service Level Objectives (SLOs).
Vulnerability management
DoubleCloud is dedicated to minimizing the impact of vulnerabilities in our products, services, and infrastructure. Our comprehensive and evolving vulnerability management approach employs automated and manual methods to identify, monitor, and resolve vulnerabilities across our applications and systems.
We discover security vulnerabilities through various sources, such as automated scanning tools, internal security assessments, customer reports, and our vulnerability disclosure program.
Infrastructure
We employ a range of vulnerability scanning tools we run regularly across our infrastructure to scan for and identify vulnerabilities automatically, including the following:
-
Network scans – to identify running services, open ports, applications, and network-level vulnerabilities across our environment.
-
Continuous asset discovery – we perform continuous discovery and security assessment of our external network boundaries and maintain an internally created asset inventory system for tracking.
-
Infrastructure Configuration Monitoring – we monitor the configuration of our cloud and infrastructure environments against established security configuration baselines.
Products
As part of our development process, we employ various techniques, including our Vulnerability Disclosure Program, to identify and resolve as many vulnerabilities and bugs as possible before our customers are impacted. These techniques include the following:
-
DoubleCloud deploys most of its services using containers and virtual machine images. We perform container and VM security scanning analyses in our CI/CD pipeline for all container and VM images deployed into our development or production environments.
-
Our products and services rely on numerous open-source libraries. We perform Software Composition Analysis and SBOM analysis to scan dependencies to identify and remediate those with security vulnerabilities.
Incident response
DoubleCloud has a well-established procedure for managing security incidents. Any instance that affects the confidentiality, integrity, or availability of customer or company data and services is considered a security incident. Our internal framework is clearly defined and includes detailed plans for various incident types, ensuring consistent and efficient response steps are taken during the entire incident response process, including detection, analysis, categorization, containment, eradication, and recovery.
Comprehensive and centralized logging and monitoring solutions of our products and infrastructure are in place to ensure we detect potential incidents in a timely manner, supported by highly qualified on-call incident managers with significant experience coordinating an effective response. We have established procedures for informing our customers in case their data is affected by a confirmed security breach. We also conduct thorough post-incident evaluations to gain insights and improve our security measures, making it more difficult for potential malicious actors in the future.
Security monitoring program
DoubleCloud has implemented a security monitoring program responding to the evolving threat landscape. This program involves proactive searches on our Security Incident and Event Management (SIEM) platform to detect malicious activity targeting DoubleCloud and our customers. These detections run on a scheduled basis to ensure the ongoing security of our systems.
Our security operations team regularly creates new detections, tunes and improves existing detections, and automates detection responses. To ensure effective threat detection capability, they do this across multiple dimensions, including products, attack types, and log sources.
The program aims to ensure that we are adequately prepared for common and sophisticated threats we encounter. For more information about our detection program, please visit this page on our DoubleCloud Trust Center
Securing our ecosystem and supply chain partners
Supplier risk management
Where DoubleCloud engages any third-party vendors (including contractors and cloud service providers), we intend to ensure those engagements do not jeopardize our customers and their data.
Our compliance, legal, and procurement teams have established a review process for any proposed third-party supplier engagements. Engagements we deem a high risk are subject to additional reviews by our privacy, security, risk, and compliance teams. Ongoing due diligence also occurs annually or during contract renewal, depending on the risk level of the third-party engagement.
Compliance and risk management
Our policy and risk management programs
DoubleCloud implements a compliance and risk management program that aligns with the ISO 27001 Information Security Management System Standard. Our program considers the security needs of our customers. It defines a tailored set of security requirements, incorporating controls from various industry-recognized standards for cybersecurity.
We consider whether these controls are appropriate for our particular product offerings, customers, and company and how to implement them effectively. Our program has two pillars as its foundations:
-
The Compliance Management Program encompasses a range of security policies designed to meet the standards outlined in ISO 27001, Service Organization Controls (SOC), and the Cloud Security Alliance's Cloud Controls Matrix (CCM). Our security policies are shared with all our teams to set expectations for security.
-
The Risk Management Program evaluates and manages ongoing risk assessments of our environments and products to identify the risks we face and ensure effective controls are implemented to manage those risks. Risk assessments are conducted annually, and we implement projects to mitigate identified risks at least quarterly.
Compliance with laws, regulations, and standards
We have developed our security program to ensure it complies with multiple industry-recognized cybersecurity standards. This assures our customers that DoubleCloud's security program meets a baseline of security controls.
Here are a few of the critical standards we comply with:
|
ISO 27001 |
ISO 27001 encompasses developing and implementing an Information Security Management System (ISMS) and then implementing and managing a suite of controls covered under |
|
CSA CCM / STAR |
The CSA Security, Trust & Assurance Registry (STAR) documents the security controls provided by various cloud computing offerings. The CSA STAR Level 1 Questionnaire for DoubleCloud is available for download on the Cloud Security Alliance’s STAR Registry |
|
GDPR |
We understand that our customers have requirements under the EU Global Data Protection Regulation (GDPR) directly impacted by their use of DoubleCloud managed services. Learn more about our approach to EU GDPR compliance on our DoubleCloud Privacy Policy page |
|
CCPA |
We appreciate that our customers have requirements under the California Consumer Protection Act (CCPA) directly impacted by their use of DoubleCloud managed services. Learn more about our approach to CCPA compliance on our DoubleCloud Privacy Policy page |
Privacy at DoubleCloud
DoubleCloud's Privacy Program ensures we meet the highest data privacy protection standards worldwide. Our data management solutions and processes are designed to help our customers meet their privacy obligations. In our Privacy Policy
-
Detailed analysis: re are dedicated to conducting Data Protection Impact Assessments to guarantee the proper handling of data, and we consult with relevant regulators when appropriate.
-
Access controls and training: DoubleCloud staff that access and process DoubleCloud customer personal data, are trained to handle it and are bound to maintain its confidentiality and security.
-
Privacy by design: we integrate privacy by design into our products. It's described further on our Customer Agreement page.
-
User profile and privacy tools: users can customize their profile settings.
Internal and external audits
Annually, we conduct thorough security assessments as part of our compliance audits. This process includes an independent external audit firm(s) evaluation and internal operational audits covering various security topics in high-risk areas. The outcomes of these audits are presented to our Security Steering Committee and used to improve our security program continuously.