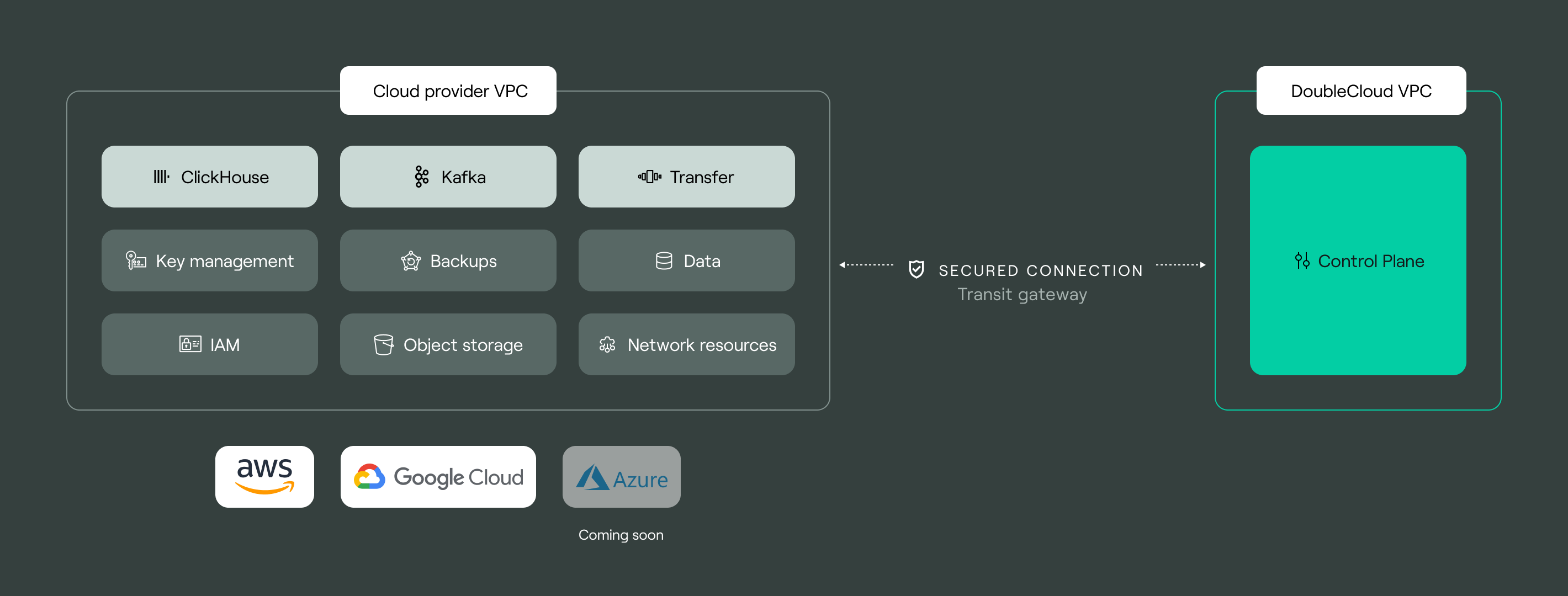
Bring your own cloud (BYOC)
When you create a cluster or transfer in DoubleCloud, it's deployed in DoubleCloud-managed infrastructure. However, if your company has strict compliance requirements or commitment discounts from the cloud provider, you can benefit from bringing your own cloud (BYOC) and running DoubleCloud resources in your existing AWS account or Google Cloud project.
BYOC supports Managed ClickHouse® clusters, Managed Apache Kafka® clusters, Managed Apache Airflow® clusters, and Transfer.
Resources that are deployed in DoubleCloud belong to VPCs that are also called internal networks. For resources created with BYOC, DoubleCloud creates custom VPCs in your cloud provider project, and these VPCs are referred to as external networks. Networks of both types are used to transmit data between cloud resources, such as clusters, and connect to the internet via peering connections.
DoubleCloud creates external networks based on the CloudFormation
DoubleCloud stack template
You can find the DoubleCloud stack template in
our S3 bucket
Why use BYOC
-
Compliance and security: BYOC is convenient when you need to keep your data only in your cloud. All the computational resources, storage, and data remain in AWS or Google Cloud, while DoubleCloud takes care of backups, monitoring, logs, and other resource management tasks.
-
Network control: with BYOC, you configure all the network elements by yourself, including VPCs, subnets, security groups, ALBs, etc.
-
Commitment discounts: if you have commitment discounts or credits from AWS or Google Cloud, you can save on computational resources, traffic, and storage.
Security
Clusters in external VPCs have several levels of protection.
-
AWS VPC security measures
When you add an external network, DoubleCloud creates several resources in your AWS account. These resources include a VPC, security groups, ACLs, route tables, and others, depending on your network configuration. The predefined parameters prevent unauthorized access to your network.
-
Allowlists in DoubleCloud
The main manually configurable access management measure is using allowlists for every cluster An allowlists enables access to the cluster only from specified IP addresses.
Tip
DoubleCloud has no access to your data. For more information, refer to Data privacy.
Pricing
When you use BYOC, the pricing is custom. You pay your cloud provider for computational resources, traffic, and storage. DoubleCloud charges a fee for managing the infrastructure.
To calculate the price, start creating a cluster and select an external VPC.